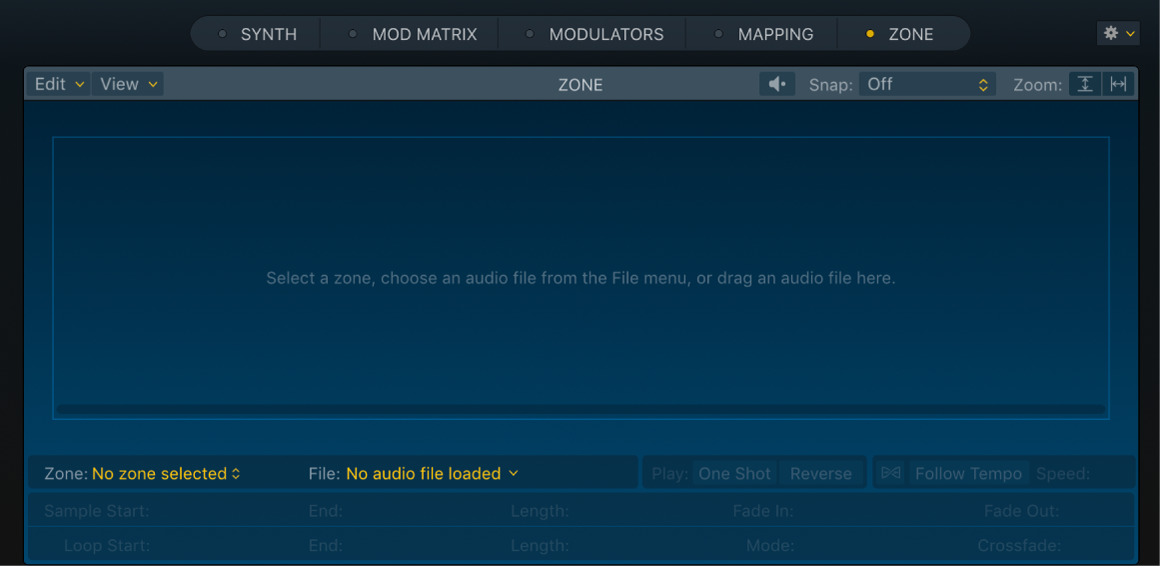
40 identify and label the following attacks by dragging the term on the left to the definition
Identify and label the following attacks by dragging the term on the ... Identify and label the following attacks by dragging the term on the left to the from CMIT- 320 at University of Maryland, University College item at position 22 identify and label the following attacks by ... 1) An attacker deceivesstaff into granting access to sensitive dataor protected systemsby posing as someone who needs or is authorizedto have that access. Whaling 2) A hacker impersonatinga reputable company sends emails to high-profile employeesrequesting them to confirm personal informationor send money. Vishing
› news › indexNews Headlines | Today's UK & World News | Daily Mail Online Oct 25, 2022 · All the latest breaking UK and world news with in-depth comment and analysis, pictures and videos from MailOnline and the Daily Mail.

Identify and label the following attacks by dragging the term on the left to the definition
Join LiveJournal Password requirements: 6 to 30 characters long; ASCII characters only (characters found on a standard US keyboard); must contain at least 4 different symbols; Test Out 3 - Subjecto.com You identify the following values: ... Match the social engineering description on the left with the appropriate attack type on the right. ... Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. News Headlines | Today's UK & World News | Daily Mail Online Oct 26, 2022 · All the latest breaking UK and world news with in-depth comment and analysis, pictures and videos from MailOnline and the Daily Mail.
Identify and label the following attacks by dragging the term on the left to the definition. › databases › questiaQuestia - Gale Individual subscriptions and access to Questia are no longer available. We apologize for any inconvenience and are here to help you find similar resources. Drag the labels from the left to their correct locations - JustAnswer Follow these steps: First, drag blue labels onto blue targets only to identify each stage of the life cycle. Next, drag pink labels onto pink targets only to identify the process by which each stage occurs. Then, drag white labels onto white targets only to identify the ploidy level at each stage. Labels can be used once, more than once, or not ... › environmentEnvironment - The Telegraph Oct 22, 2022 · Water meters should be compulsory and bills should rise, says new Environment Agency chairman. Alan Lovell says households consume too much water and metering is needed to encourage them to cut ... › createJoin LiveJournal Password requirements: 6 to 30 characters long; ASCII characters only (characters found on a standard US keyboard); must contain at least 4 different symbols;
› blog › depression-cant-beWhen Depression Can’t Be Cured, You Can Still Cope Feb 09, 2012 · Its by definition exactly that. and more than that, I find it morally repulsive, and find that people illing to leave someone they claim to love at their darkest hour for the sake of their on ... When Depression Can’t Be Cured, You Can Still Cope Feb 9, 2012 · Its by definition exactly that. and more than that, I find it morally repulsive, and find that people illing to leave someone they claim to love at their darkest hour for the sake of their on ... learn.microsoft.com › en-us › dynamics-gpSystem Setup Guide - Dynamics GP | Microsoft Learn Aug 01, 2022 · Check the navigation panel to the left to get an overview of available material. In addition to defining a schedule for setting up and using the software, many businesses make detailed assignments for specific tasks, such as defining customer and vendor numbers, creating vendor, item and customer records, entering and posting beginning balances. CyberSecurity Chapter 3 Flashcards | Quizlet You have recently discovered that a network attack has compromised your database server. Te attacker may have stolen customer credit card numbers. You have stopped the attack and implemented security measures to prevent the same incident from occurring in the future. What else might you be legally required to do
System Setup Guide - Dynamics GP | Microsoft Learn Aug 1, 2022 · The term "workflow" can therefore refer to multiple, related things. Workflow is the sequence of actions that leads to the completion of a business task. The sequence is carried out according to a set of rules or policies. ... User records identify all the people who will be using Microsoft Dynamics GP. ... Use the Account Definition Setup List ... › archivesInquirer.com: Philadelphia local news, sports, jobs, cars, homes Keep reading by creating a free account or signing in.. Sign in/Sign up; Subscribe; Support local news; News Sports Betting Business Opinion Politics Entertainment Life Food Health Real Estate Obituaries Jobs Questia - Gale Individual subscriptions and access to Questia are no longer available. We apologize for any inconvenience and are here to help you find similar resources. Android 12 Compatibility Definition - Android Open Source Project Oct 25, 2022 · Android device implementations are classified as a Handheld if they meet all the following criteria: Have a power source that provides mobility, such as a battery. Have a physical diagonal screen size in the range of 3.3 inches (or 2.5 inches for device implementations which shipped on API level 29 or earlier) to 8 inches.
Environment - The Telegraph Oct 22, 2022 · Water meters should be compulsory and bills should rise, says new Environment Agency chairman. Alan Lovell says households consume too much water and metering is needed to encourage them to cut ...
Identify and label the following attacks by dragging the term on the ... masqueradingmasqueradingan attacker pretending to be from a trusted organization sends emails to senior executives andan attacker pretending to be from a trusted organization sends emails to senior executives andhigh-profile personnel asking them to verify personal information or send money.high-profile personnel asking them to verify personal …
U.S. News | Latest National News, Videos & Photos - ABC News - ABC News Oct 23, 2022 · The NYPD released footage of the unprovoked attack. Emilia "Amy" Marin told ABC News of her struggles in the tragedy's aftermath. The popular tourist attraction is located about 200 feet below ...
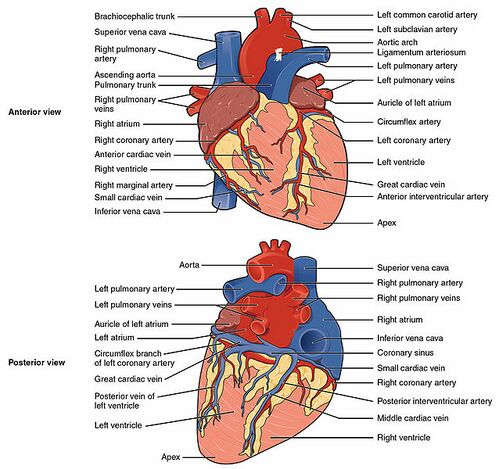
Solved Correctly label the following planes. Frontal plane - Chegg Frontal plane Sagittal plane Transverse plane Click and drag the labels to identify the nine regions of the abdomen. Regions Left hypochondriac region Umbilical region Left inguinal region Epigastric region hypochondriac region Left lumbar region Hypogastric region Right lumbar region Right inguinal region Label the
Solved Drag and drop the labels onto the figure to identify - Chegg Expert Answer. P wave. QRS wave. T wave. Aortic pres …. View the full answer. Transcribed image text: Drag and drop the labels onto the figure to identify the events associated with the cardiac cycle. Use each label once. View Available Hint (s) Reset Help P wave I wave QRS wave Left atrial pressure diastolic Veitin dhe systolic pressure ...
3.5 Flashcards | Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. 1) An attacker convinces personnel to grant access to sensitive information or protected systems by pretending to be someone who is authorized and/or requires that access. Masquerading
Inquirer.com: Philadelphia local news, sports, jobs, cars, homes Keep reading by creating a free account or signing in.. Sign in/Sign up; Subscribe; Support local news; News Sports Betting Business Opinion Politics Entertainment Life Food Health Real Estate Obituaries Jobs
News Headlines | Today's UK & World News | Daily Mail Online Oct 25, 2022 · All the latest breaking UK and world news with in-depth comment and analysis, pictures and videos from MailOnline and the Daily Mail.
News Headlines | Today's UK & World News | Daily Mail Online Oct 26, 2022 · All the latest breaking UK and world news with in-depth comment and analysis, pictures and videos from MailOnline and the Daily Mail.
Test Out 3 - Subjecto.com You identify the following values: ... Match the social engineering description on the left with the appropriate attack type on the right. ... Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used.
Join LiveJournal Password requirements: 6 to 30 characters long; ASCII characters only (characters found on a standard US keyboard); must contain at least 4 different symbols;













0 Response to "40 identify and label the following attacks by dragging the term on the left to the definition"
Post a Comment